IIoT cybersecurity for travel companies
While global travel and travel workforces have been reduced as a result of the COVID-19 crisis, threat activity against the aviation sector has not. A case in point is a March 2020 data breach disclosed by the San Francisco International Airport. Reportedly, the attack was perpetrated by Russia’s state-sponsored hacking group Dragonfly. This group typically targets organizations in critical infrastructure sectors with the objectives of reconnaissance, lateral movement, and cyber espionage.
Sustaining and securing critical infrastructures – such as those shared by travel and transportation companies – have always been challenges. The addition of COVID-19-related concerns has strained companies’ security, resiliency, and continuity plans to their limits. While the industry will recover from COVID-19, it may never be immune to cyber attacks. Overcoming this global challenge requires adaptability and innovative security and risk management practices.
 The travel industry is an attractive target for malicious actors. The reliance on information technology (IT) to facilitate operations, the ubiquitous need for integration of third-party vendors, and the global scope and integration of the travel supply chain represent a large, diversified attack surface.
The travel industry is an attractive target for malicious actors. The reliance on information technology (IT) to facilitate operations, the ubiquitous need for integration of third-party vendors, and the global scope and integration of the travel supply chain represent a large, diversified attack surface.
IIoT benefits… and risks
Many travel providers rely on Industrial Internet of Things (IIoT) solutions to manage complex operations. Use of these IIoT platforms and services increases the potential for unauthorized access to proprietary data and critical systems that can disrupt physical assets.
Numerous travel companies also are dependent on legacy IT systems, some with critical software vulnerabilities. Because they are difficult to update, these systems are inherently vulnerable, yet firms connect IIoT devices to them for operational applications, including some used by travelers.
Whether executed by financially motivated cybercriminals or politically motivated nation-states, a successful attack on a segment of the travel industry can result in severe cascading effects that can influence aggregate travel demand and, thus, the entire global economy. As attack vectors multiply, and critical vulnerabilities are exploited in short order, risks grow exponentially — often rapidly and without precedent.
In addition, as ecosystems grow, companies become even more vulnerable. And continued innovation across the industry makes it likely the travel ecosystem will continue to expand and evolve. To prepare for the future, travel organizations should focus on improving their cyber resilience today.
The travel industry security landscape
To better understand what makes some organizations more secure and cyber resilient than others, the IBM Institute for Business Value, in cooperation with Oxford Economics, surveyed IT and operational technology leaders from travel organizations across the globe. Our findings confirm the rapid adoption of IIoT technologies in a wide variety of functional areas.
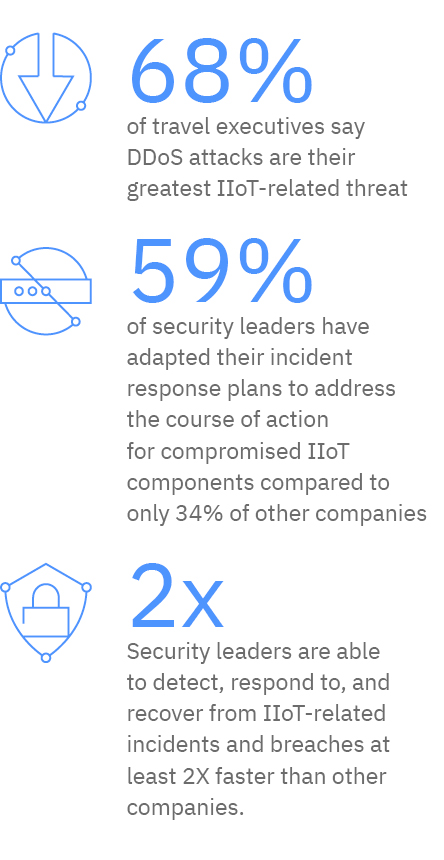
Many companies are applying these technologies in their supply chain and logistics processes – for fleet management, predictive maintenance, and location management. However, executives are apprehensive about the security of information flowing between their operational, corporate IT, and IIoT networks. Gateways and gateway-related connectivity represent almost half of the most vulnerable IIoT components reported by travel companies.

While travel providers might be aware of the risks, many continue to deploy IIoT technologies faster than they can secure them. We found that almost two thirds of surveyed executives say they have, at a minimum, the capabilities to provide new IIoT-enabled offerings and services, yet only half say they can do so in a secure manner.
Learning from security leaders
Using our survey data, we identified a group of companies we deem “security leaders” based on their IIoT cybersecurity budgets, known vulnerabilities addressed by security controls, and response and recovery times. What truly differentiates security leaders from the other companies from the survey is their cyber resilience: they are able to detect, respond to, and recover from IIoT-related incidents at least twice as fast as other companies.

Using our study data and analysis of the security leaders, we identified ten security controls and AI-driven practices that can positively impact IIoT cybersecurity performance. Read the report for recommendations on how travel companies can implement them as part of a two-phase approach to improve their IIoT cybersecurity postures and resilience.
Meet the authors
Eric Maass, Director of Strategy and Emerging Technology, IBM Security ServicesSteven Peterson, Global Thought Leader, IBM Institute for Business Value
Lisa-Giane Fisher, Leader, Middle East and Africa, and Global Benchmark Research leader, Utilities industry, IBM Institute for Business Value
Gerald Parham, Global Research Leader, Security and CIO, IBM Institute for Business Value
Greg Land, IBM Global Industry Leader, Aviation, Hospitality and Travel Related Services
Julian Meyrick, Managing Partner & Vice President, Security Strategy Risk & Compliance, IBM
Download report translations
Originally published 30 April 2020


